Cyber Security and Vehicle Communications
Darcy Conlin
This is our second article highlighting the work being done at Utah State University under Electrical and Computer Engineering Assistant Professor Ryan Gerdes. Our previous article introduced the platooning research and testing that is currently underway at USU. This article will take a closer look at the electronic communication within a vehicle and between vehicles. We were able to sit in on a discussion with Professor Gerdes and eTrans Chief Security Office Manuel Villar. The two shared their experience, concern and hopes in moving forward with the development of secure electronic communications among our future vehicles. While isolated vehicles are noteworthy from a security perspective, what is more intriguing to these two gentlemen is when you have a group of vehicles that are interacting together.
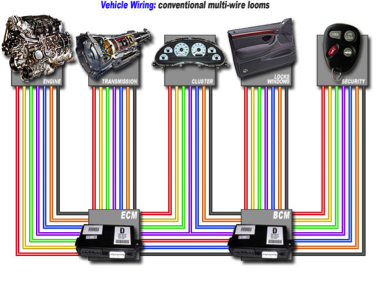
There is a growing need for our automobile manufacturers to be in sync with cyber security experts to develop safe and secure vehicle communications. Electronics were slowly introduced over the first 100 years of the automobile’s existence to make our cars run better and improve our own personal comfort, but the systems worked independently. Then in 1980, GM introduced a data communication link from one electronic module to another within the Cadillac [1]. The link was one wire, point to point, linking the engine control module to the fuel data panel[2]. Thus began the intricate communications system that interconnects electronic components inside a vehicle. The term for this specialized network is a CAN bus.
As background, CAN (also referred to as CANbus or CAN bus) is a network used in every-day products consisting of multiple microcontrollers that need to communicate with each other[3]. Robert Bosch originally created CAN in 1986. The CAN data link layer protocol is the communication system you will find in most passenger vehicle control systems. Click here to read more about CAN from CiA (CAN in Automation). CAN is implemented in hardware in the microcontrollers of about 25 chip manufacturers[4]. The BMW 850 coupe is noted as the first CAN Bus vehicle to enter the market in 1986.
Both Villar and Gerdes agree that CAN is not designed with any inherent security. Through their eyes, it has been surprising to see the type of information that was going across these buses and the fact that it wasn’t segmented. For example, the infotainment system of a vehicle was on the same bus as the engine control. In Gerdes’ words “there’s no confidentiality, no integrity and no assurance here.” Researchers have found that by reverse engineering they can easily gain access to this surplus of electronic communication. And when someone has access to that information, they have access to control those parts of the vehicle, for example, to turn the engine off. BAM! This has the potential for obvious problems.
When vehicles were isolated systems, this wasn’t much of an issue. However, as vehicles become more connected whether through infotainment systems, Bluetooth connections or the DSRC safety systems the government is planning to mandate, controlling access to and securing the electronics in the vehicle becomes much more important. In addition, Professor Gerdes believes that in order to increase safety on our roads we’re going to need to get vehicles traveling closer together, or platooning. Unless we’re going to build more roads and better drivers (which doesn’t seem very likely, at least until we get driverless vehicles), we need to make platooning a reality so that a greater number of vehicles can take up the road with the existing infrastructure.
In order for vehicles to travel safely together in a platoon, they need to talk to each other. That talking includes sharing some digital information. As we’ve noted, connected vehicles represent a security concern. This is where a public key infrastructure (PKI) comes into play. A PKI involves a set of hardware, software, policies and standards that are required to create, manage and distribute digital certificates. The digital passing - - and parsing - - of all connected vehicle (CV) information requires a trustworthy PKI. Mr. Villar recognized that plenty of security and technology experts are trying to develop the PKI for CV’s with low bandwidth. However, with so many keys out on the infrastructure that may be unrealistic.
Gerdes agreed. He added that this is the reason that part of his research work is to enable peer-to-peer security[5]. Peers are equally privileged, equipotent participants in the application. Within this P2P, a secure key exchange needs to be created. Gerdes states, “We have some ideas for both key generation and the exchange between vehicles that are traveling together in a group. They don’t require trust and infrastructure since your establishing keys within a group of vehicles surrounding you. We want to be sure that the protocols are resistant to a super majority of attackers at any one time.”
This P2P system is both hardware and software. Gerdes says that given the way radios are built today, they may not require a modification. It would make use of physical layer security, hardware security, as well as some traditional network security.
Villar: Do you see this residing on the communication layer or on the CAN bus itself?
Gerdes: It would have to talk to the CAN bus because it needs to tell other components, “I’m not going to forward you a message from this radio.” But it would actually be contained within the radio.
Villar: If you are communicating with the different systems on the bus, how do you not flood the CAN bus with messages that could potentially effect the time of response for life safety systems?
Gerdes: I don’t advocate using the same bus that all the other components in the vehicle are using. I’m in favor of segmenting our systems as much as possible.
The essential goal here is to build these systems to be secure from inception. No one is pointing fingers at the great engineers of our auto manufacturing companies. It is simply that these issues have not been of concern until we started discussing how to connect our vehicles and let them talk to each other. In the past our auto manufacturers didn’t have to think much about anyone gaining access to these systems except for repairs. As we begin to look into the future, that is clearly not the case. Villar concurs, “CAN is like any server or any system, if I can get my hands on it, I can own it.” Gerdes likened it to how we used to think about firewalls. “We used to think a firewall was a hard protective shell, but on the inside, since you have this hard protective shell, you just leave everything soft and really easy to break into, left completely unprotected. “
Our vehicle electronic systems are at a crossroad and our technology and automobile industries are in the middle of that intersection. It’s imperative that security research such as what Gerdes manages at USU, and the cyber security expertise that Villar possesses both continue to scrutinize these systems to ensure they are secure from the onset. Let’s keep the conversations going. Stayed tuned to Driverless Transportation as we hope to get Villar and Gerdes together again this spring out in Utah to test some of their theories.
[1] http://en.wikipedia.org/wiki/Vehicle_bus
[2] Ronald W. Cox, Local Area Network Technology Applied to Automotive Electronics Communications, IEEE Transactions on Industrial Electronics, VOL. IE-32, No. 4, November 1985, Page 327-333
[3] http://www.canbus.us
[4] http://www.canbus.us
[5] peer-to-peer (P2P) networking is a distributed application architecture that partitions tasks or work loads between peers.